Snowflake
Introduction#
Multi-factor authentication (MFA) is an extra layer of security used when logging into websites or apps to authenticate users through more than one required security and validation procedure that only they know or have access to. Security Assertion Markup Language (SAML) is a protocol for authenticating to web applications. SAML allows federated apps and organizations to communicate and trust one another’s users.
Acceptto™, as a SAML provider, improves the user login experience for Snowflake users with its convenient SSO-MFA solution.
Pre-Requisites#
- An Acceptto account with a configured Identity Provider and LDAP Agent (See this page for instructions).
- A Snowflake user account with ACCOUNTADMIN role.
- A user with administrative privileges for the Acceptto Cloud dashboard.
Configure Snowflake as a Service Provider#
Download the SAML metadata and certificate for your organization from Acceptto.
Metadata Download at
https://sso.acceptto.com/<myorganization>/saml/download/metadataor view athttps://sso.acceptto.com/<myorganization>/saml/metadataCertificate Download at
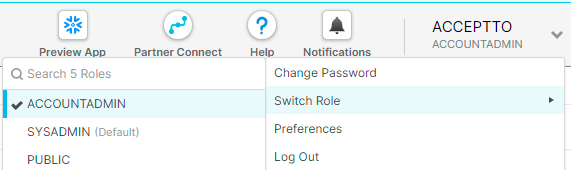
https://sso.acceptto.com/<myorganization>/saml/download/certLog into your Snowflake instance as an administrator. Switch the user role from SYSADMIN (Default) to ACCOUNTADMIN using the Switch Role menu located under your account name, on the right-hand side of the screen.
Navigate to the Worksheets section and paste the following query with information acquired earlier from Acceptto.
use role accountadmin;CREATE SECURITY INTEGRATION AccepttoINTEGRATION TYPE = SAML2 ENABLED = TRUE SAML2_ISSUER = “https://sso.acceptto.com/<myorganization>/saml” SAML2_SSO_URL = “https://sso.acceptto.com/<myorganization>/saml/auth” SAML2_PROVIDER = Custom SAML2_X509_CERT = “copy/paste Acceptto certificate value within Begin and End title” SAML2_SP_INITIATED_LOGIN_PAGE_LABEL = AccepttoSSO SAML2_ENABLE_SP_INITIATED = TRUE;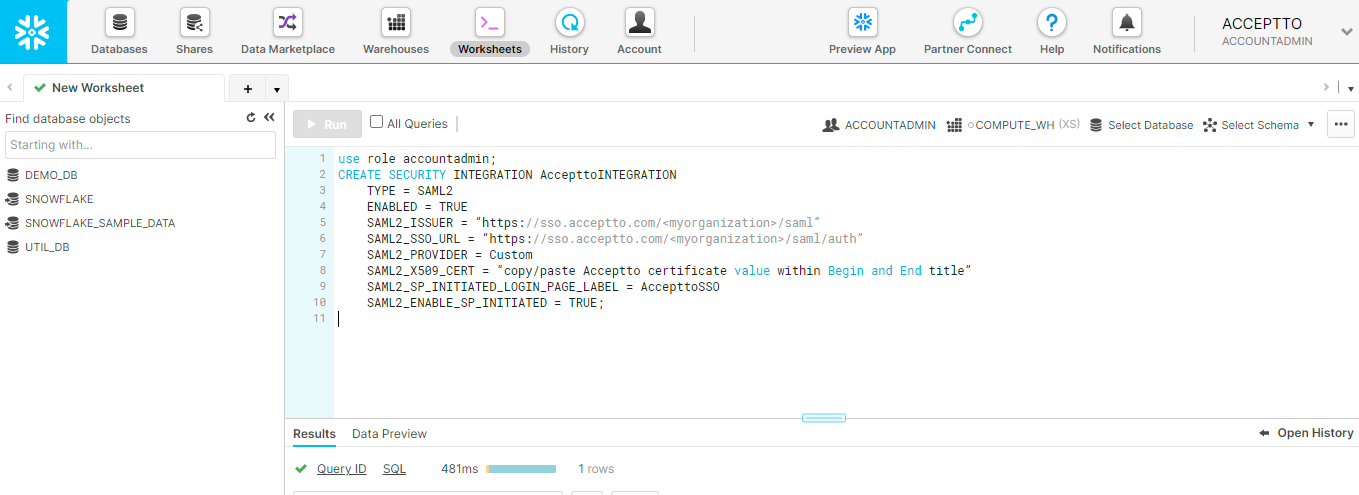
Click on the Run button and execute the query.
Delete the previous query and run the below one to enable SSO through the Snowflake login page.
use role accountadmin;alter account set sso_login_page = true;We will now create users who are going to log into Snowflake. Navigate to the Account section.
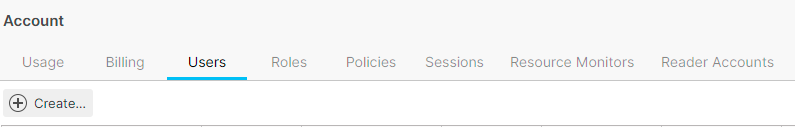
Select the Users tab and click on the Create button.
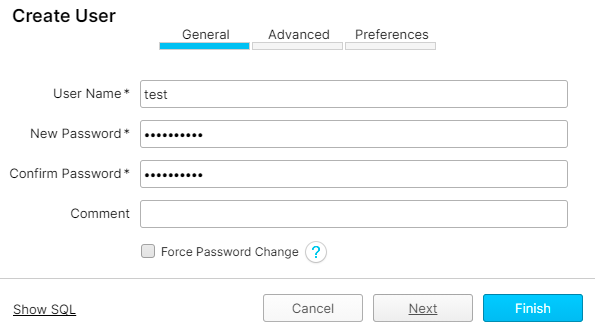
In the Create User dialog box on the General tab, fill the Username and Password fields and uncheck Force Password Change. Click on Next.
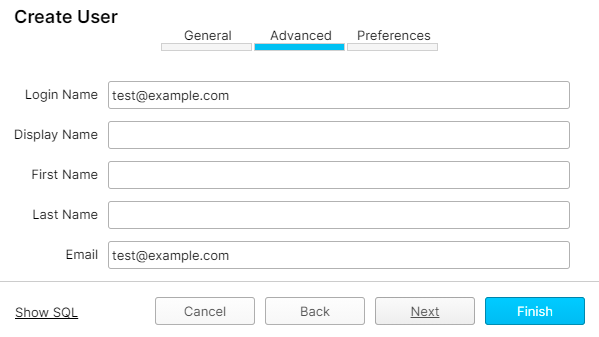
On the Advanced tab, fill the Login Name and Email fields. Click on Next (Note that your login name and email address should be the same with your username and email address on the directory service).
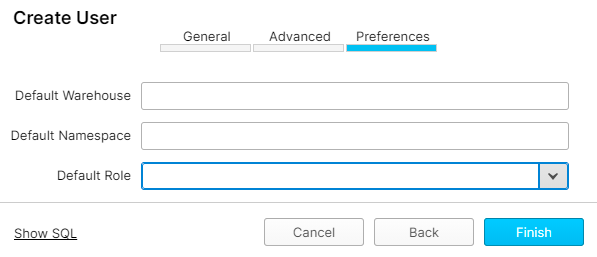
On the Preferences tab, select the user’s role in the Default Role dropdown and click Finish.
It is recommended by Snowflake to unset a new user password for login through SSO. Go to the Worksheets section and run the following command:
alter user <name> unset password;
Acceptto SAML Configuration as Identity Provider (IdP)#
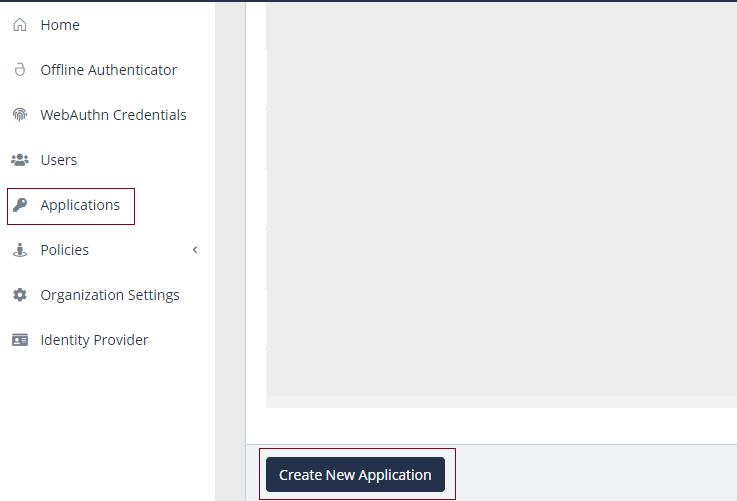
Log into the Acceptto Dashboard with an administrative account and go to the Applications.
Create a new application by selecting the Create New Application.
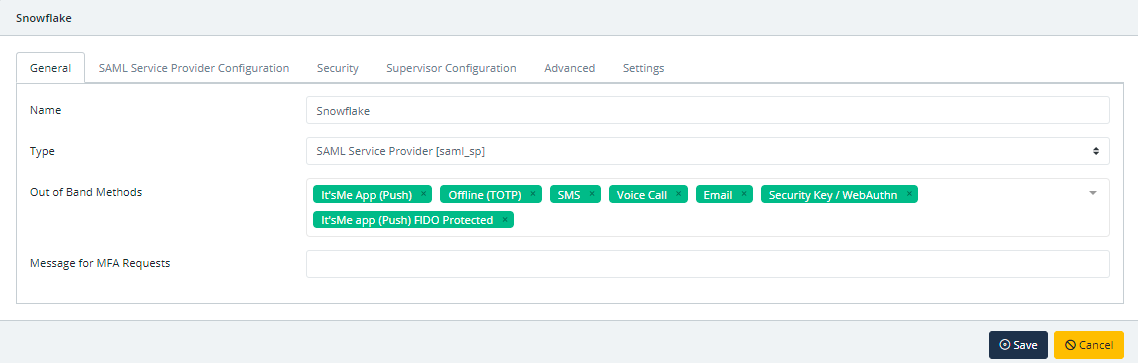
In the New Application form, enter the following values under the General tab.
- Name - The application name displayed in the admin panel and application portal and used for push notifications and audit logs (e.g. Snowflake).
- Type - Select "SAML Service Provider" from the options.
- Out of Band Methods - Select the allowed methods for approving MFA requests
- Message for MFA Requests - Enter the user-facing message for Push, SMS, and email MFA requests (optional)
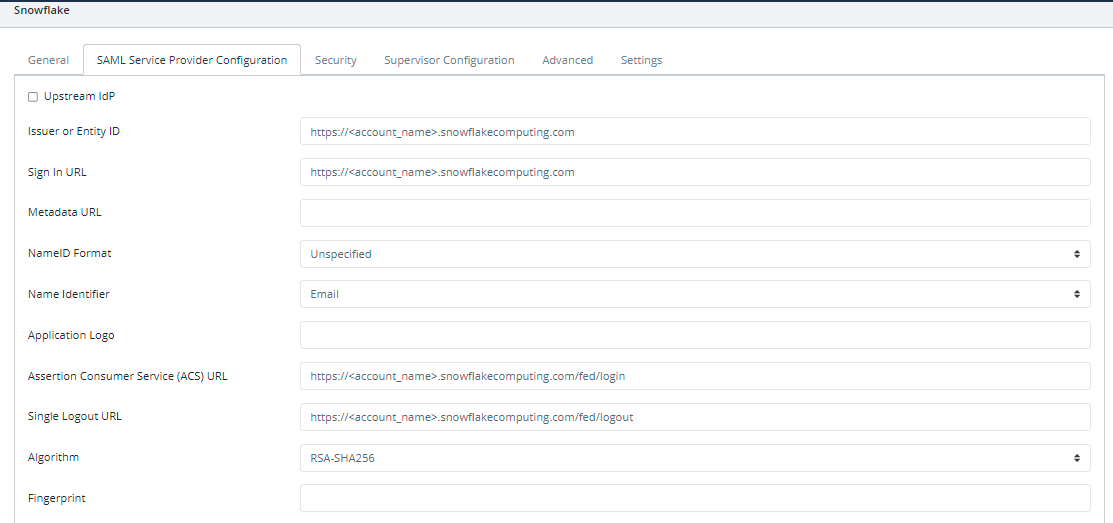
Under the SAML Service Provider Configuration tab, enter the following values:
- Issuer or Entity ID – The Issuer/EntityID of your Snowflake instance.
If your account is in US West:
https://<account_name>.Snowflakecomputing.comIf your account is in any other Snowflake Region:https://<account_name>.<region_id>.Snowflakecomputing.com - Sign in URL - Same as Issuer or Entity ID.
- NameID Format - Unspecified.
- Name Identifier - Email.
- ACS URL - The Assertion Consumer Service URL of your Snowflake instance.
If your account is in US West:
https://<account_name>.Snowflakecomputing.com/fed/loginIf your account is in any other Snowflake Region:https://<account_name>.<region_id>.Snowflakecomputing.com/fed/login - Single Logout URL - The Single Logout URL of your Snowflake instance.
If your account is in US West:
https://<account_name>.Snowflakecomputing.com/fed/logoutIf your account is in any other Snowflake Region:https://<account_name>.<region_id>.Snowflakecomputing.com/fed/logout
- Issuer or Entity ID – The Issuer/EntityID of your Snowflake instance.
If your account is in US West:
Click on Save.
Test Your Setup#
Go to your Snowflake instance and select Sign in using AccepttoSSO.
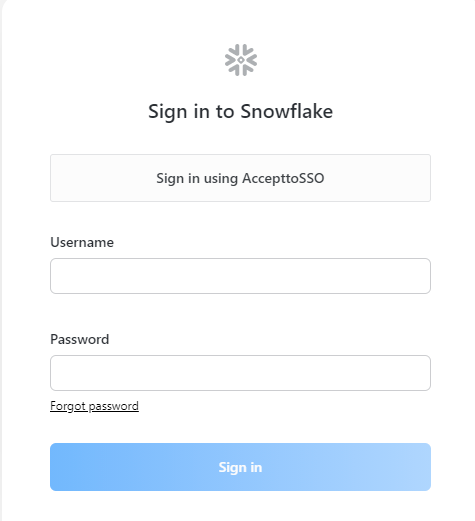
You will be redirected to the Acceptto SSO page.
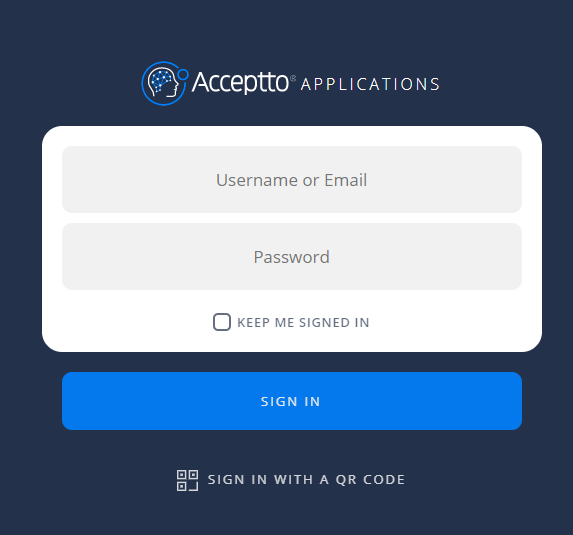
After successful authentication, you’ll see the Acceptto MFA options. Select the desired method of authentication.
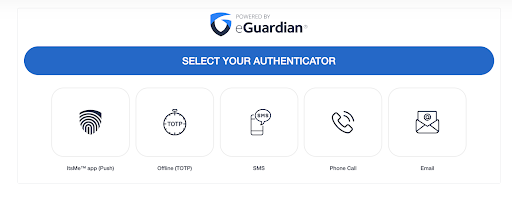
After approving the authentication request, you will be logged into your Snowflake workspace.
Support#
If you require assistance, please email us at support@acceptto.com
Sales#
Want to learn more about our MFA solutions? Contact our Professional Services for a Demo today.
Disclaimer#
All product names, trademarks, and registered trademarks are the property of their respective owners.
All company, product, and service names used in this document are for identification purposes only. The use of these names, trademarks, and brands do not constitute an endorsement by the Acceptto Corporation.