SAML Service Provider
Introduction#
This guide gives an overview of how to configure an application to work with Acceptto’s SSO service, which allows access to the application using Acceptto™ authentication technology. You will be configuring your application to act as a Service Provider and configuring Acceptto to act as an Identity Provider.
Requirements#
- Acceptto Appliance configured to connect to your user directory
- An Acceptto Organization account, with access to an administrative user
- An application that supports SAML 2.0 authentication
IdP Initiated login Architecture#
To have access to a portal containing a list of federated Service Providers (also referred to as applications). The IdP initiated login method is applied when a user logs directly to the IdP.
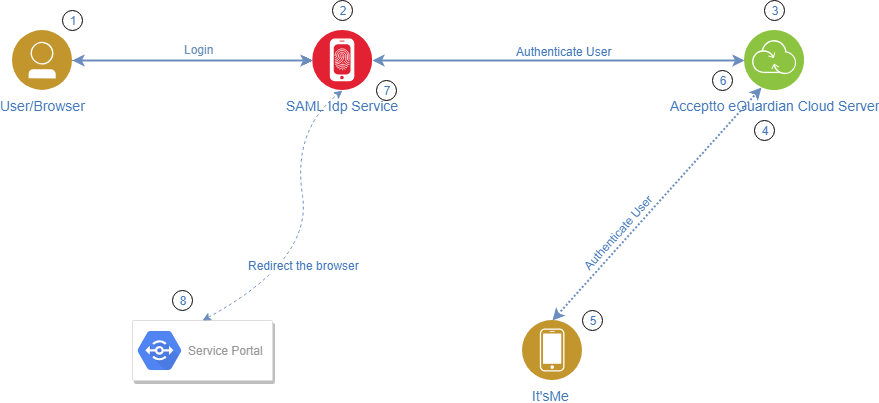
- The user accesses the IdP URL, for example, idp.acceptto.com.
- The IdP requests the user to provide credentials.
- The IdP authenticates the user against eGuardian.
- eGuardian evaluates policies and sends an out of band authentication request to It’sMe.
- The user approves the login attempt.
- eGuardian returns the result of the authentication.
- The IdP generates a signed assertion stating that the user is authenticated and has access to the Service Portal.
- The Service Portal verifies the assertion and allows the user access.
SP Initiated login Architecture#
The SP initiated login method is applied when a user accesses a federated service (SP) directly and is redirected to authenticate to the IdP before access is granted.
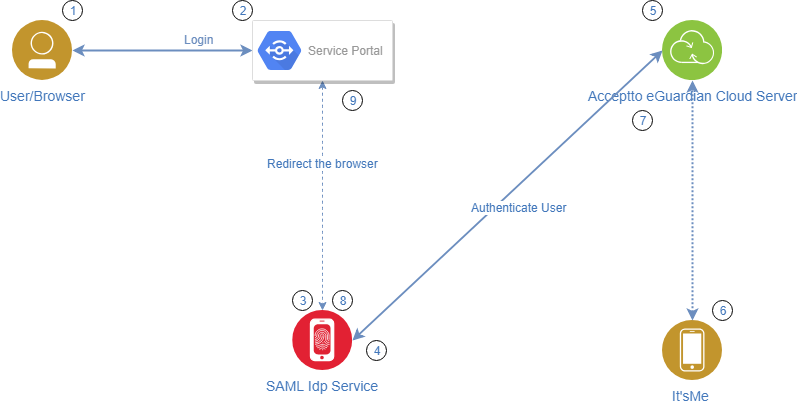
- The user accesses the Service Portal, for example, sp.acceptto.com.
- The SP redirects the user to the IdP.
- The IdP requests user credentials.
- The IdP sends an authentication request to eGuardian.
- eGuardian evaluates policies and sends an out of band authentication request to It’sMe.
- The user approves the transaction.
- eGuardian returns the result of the authentication to the IdP.
- The IdP generates a signed assertion stating that the user is authenticated and has access to the Service Portal.
- The Service Portal verifies the assertion and allows the user access.
Set Up a SAML Application#
- Login to Acceptto with a user account that has administrative privileges.
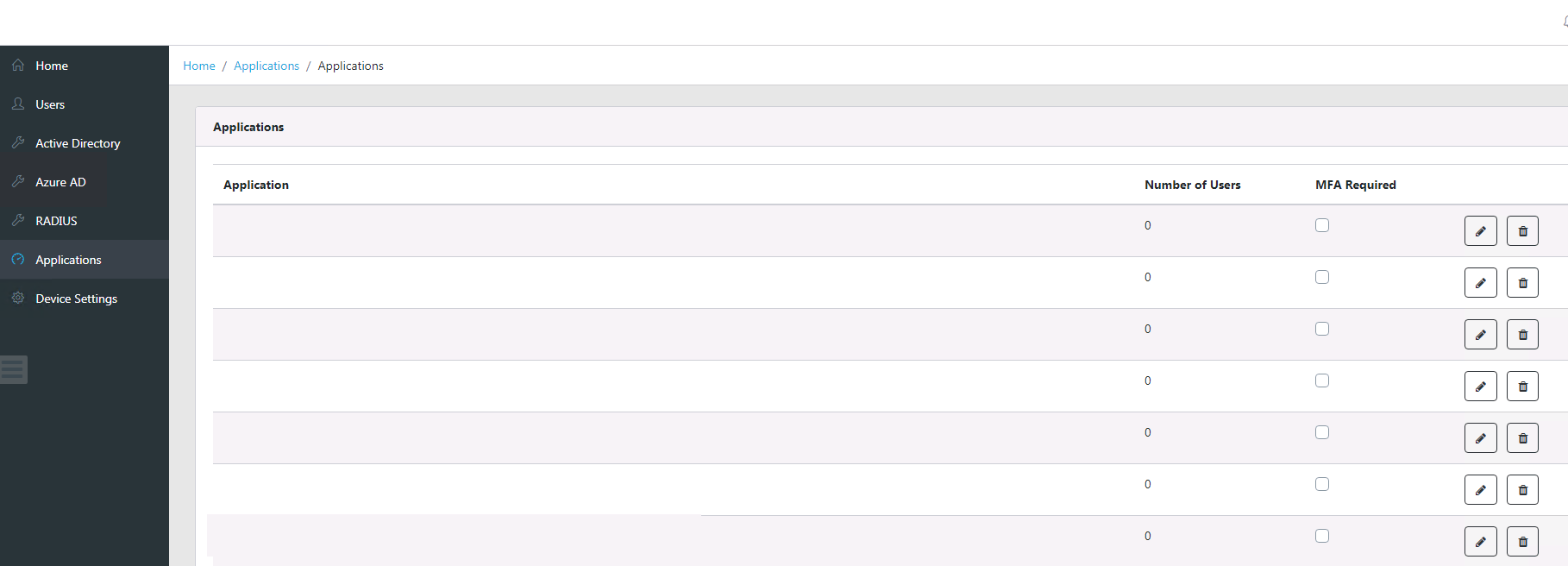
- Click on the “Applications” option on the menu bar.
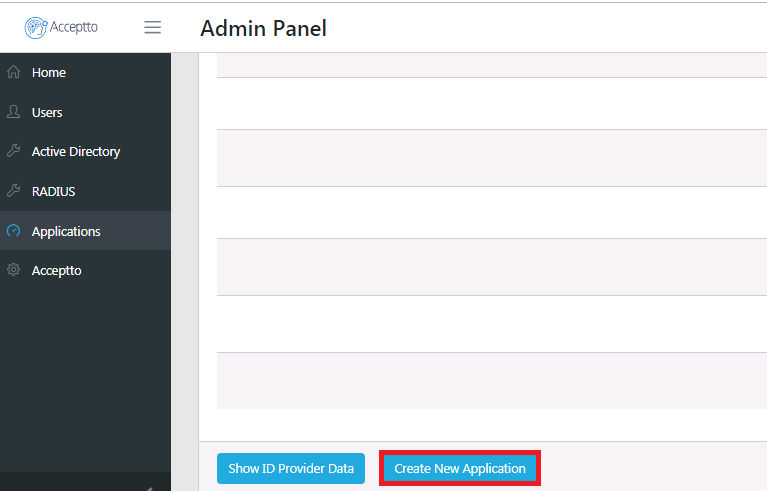
Click on the “Create New Application” button
On the “Add Application” form, enter the following:
App Name - Application name to be displayed in the admin panel and application portal Issuer or EntityID - The Issuer/EntityID of the SAML application. For example: ‘google.com/a/org.com’ Sign In URL - The URL used to sign in to the application
Metadata URL - The URL that includes that SAML application metadataClick “Save” to create the application.
Note: Clicking the “Advanced Options” button allows additional optional configuration such as encryption certificates or custom attribute assertions.
Configure your SAML Application with Acceptto#
Select Applications in the menu then click Show ID Provider Data and copy the certificate from the displayed data.
Use the configuration data in the settings page to configure your application
Identity Provider Issuer. The name of the issuer of the SAML. It may be referred to as the “EntityID” or “Idp Name”
Single Sign-On URL. The URL the SP uses to send SAML requests. It may be referred to as the “SAML Endpoint” or “SSO URL”
X509 Certificate. The certificate used to validate SAML tokens NameIdFormat. The user name format in which the user’s identity is asserted to the SAML applicationUsing the above data, configure your application according to the vendor instructions.
If your application requires any additional attribute assertions, please access the admin panel and add these via the “Advanced Options” button on the “Add Application.”
It is recommended to test your application by configuring a separate URL in addition to the usual authentication URL, to test SAML while leaving the local authentication option available.
Support#
If you require assistance, please email us at support@acceptto.com
Sales#
Want to learn more about our MFA solutions? Contact our Professional Services for a Demo today.
Disclaimer#
All product names, trademarks, and registered trademarks are the property of their respective owners.
All company, product, and service names used in this document are for identification purposes only. The use of these names, trademarks, and brands do not constitute an endorsement by the Acceptto Corporation.